
By John Himor
With cybercrime accounting for 43 per cent of overall crime in Singapore in 2020, protecting personal data has become a top priority for businesses across industries. From phishing to data breaches and cyber security attacks in Singapore, individuals, ICT personnel and companies must remain vigilant and informed on how to guard against such crimes.
To help companies stay up to date with potential lurking cyber threats and to equip them with the tools to protect themselves against data breaches, the Personal Data Protection Commission (PDPC) recently released an easy-to-use handbook and checklists. Developed in collaboration with the Cyber Security Agency of Singapore (CSA), the handbook and checklists are a robust reference for companies to keep consumer and business data safe.
Read on to find out more about how the handbook and checklists can help your organisation protect against Singapore’s most common data breaches.
Keeping watch for the five most common data breaches
The first step in guarding against data breaches is to know where the problems lie. After all, gaps in ICT system management and processes can prove risky and must be stamped out quickly. Once your organisation’s ICT personnel are aware of the issues, they can put into place new practices that directly address potential cyber security problems.
The handbook, How to Guard Against Common Types of Data Breaches, identifies the five most common gaps in organisational systems that can lead to data breaches, collated from past cases handled by the PDPC. The handbook explains the problem, provides case examples for each issue and illustrates actionable recommendations to help your organisation apply secure practices in your systems and processes.
According to the handbook, coding issues are the most common ICT gap. They are often made while programming company software—leading to errors that can result in personal data leaks. With the handbook’s help, if your organisation is experiencing this issue, you can find out what to do to plug the gaps and prevent future data breaches.
For example, the guide recommends that organisations design before coding and perform a thorough analysis of any change that might affect security. Alternatively, to provide businesses with more options and anticipate alternative scenarios, the guide also suggests investing more effort in documenting, ensuring applications are thoroughly tested and performing code reviews.
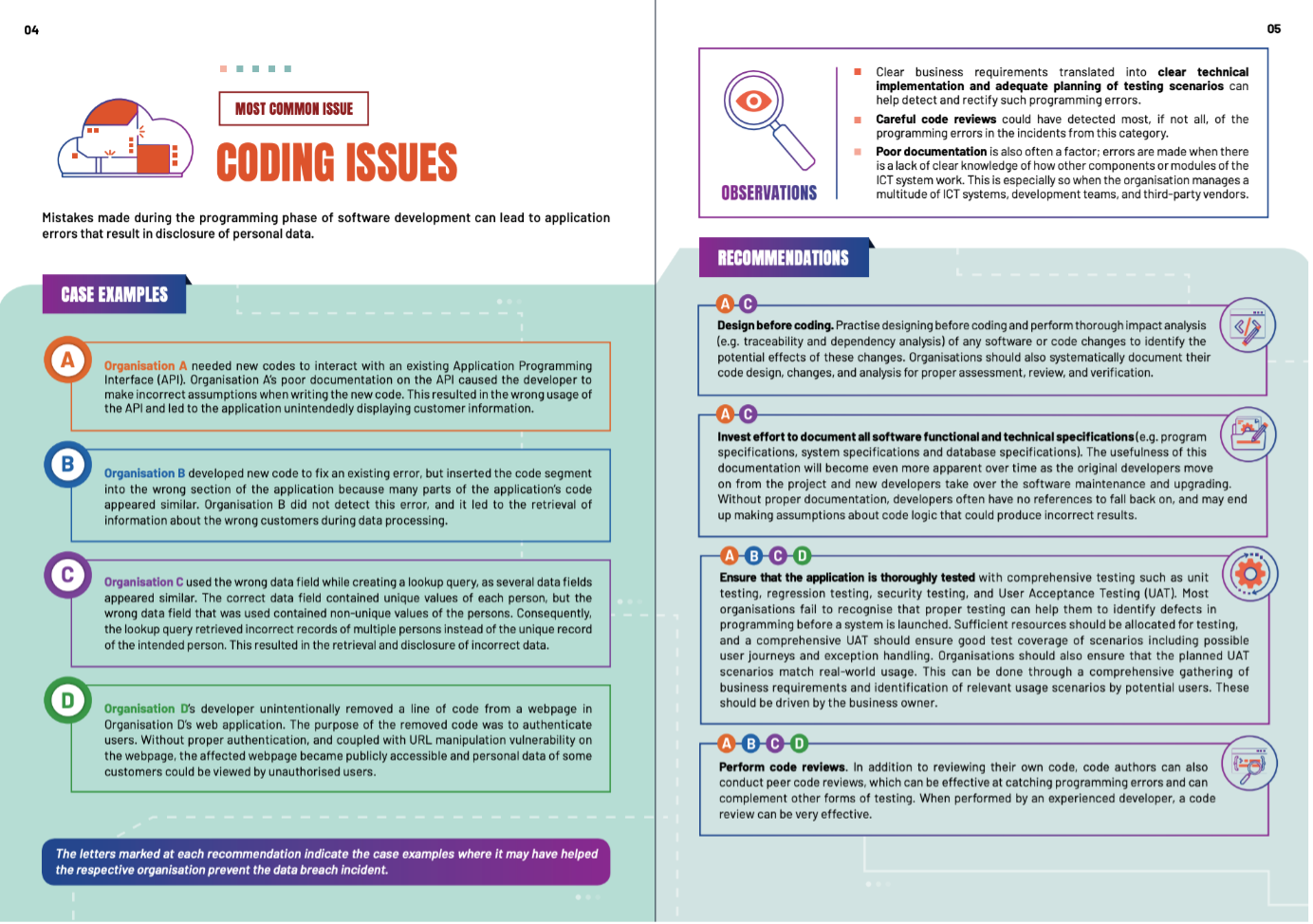
Making the most of PDPC suggestions
Similarly, your organisation can also refer to the handbook to learn how to handle other major ICT problems like configuration issues, malware and phishing, cyber security attacks and responsibility issues as well as managing accounts and passwords.
When it comes to malware and phishing, the guide explains that employees can be vulnerable to malicious links sent through unassuming emails. Among a slew of recommendations, organisations are advised to educate employees to be alert to such attacks as well as install endpoint security solutions to defend against malware.
By following the recommendations offered by the handbook, your business can achieve a baseline level of data protection, paving the way for more specific initiatives to further strengthen cyber security.
Once your organisation’s ICT personnel are familiar with the common data breaches to look out for, they can then leverage the information in IMDA’s Guide to Data Protection Practices for ICT Systems. This additional guide offers further information and good practices to set up a robust and resilient ICT system.
The guide covers data protection practices across different situations and sections, such as risk management, ICT controls and IT operations. For companies that handle personal data like names and email addresses for generic purposes, basic practices like regular risk controls and collecting minimal personal data are enough to stay secure.
Meanwhile, if your company handles more sensitive data like credit card information, enhanced practices like implementing intrusion detection or prevention systems are recommended.
Setting up security with two comprehensive checklists
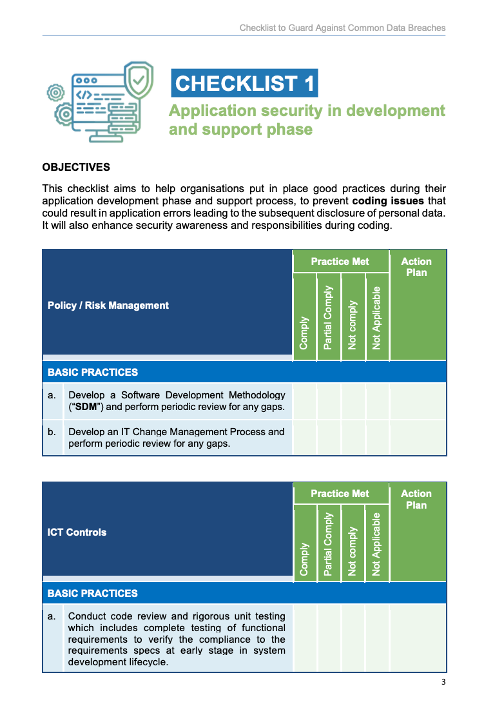
Designed to work in tandem with the handbook are PDPC’s Checklists to Guard Against Common Types of Data Breaches. The checklists are a convenient resource for organisations to review the strength and security of their systems against potential data breaches. By going through these checklists, your company can evaluate whether it has the right internal policies, technology controls and processes to address common gaps detailed in the handbook.
These checklists present multiple best practices, both basic and enhanced, that the PDPC recommends for bolstering the company’s cyber security. Once your company has assessed their compliance with these practices, it can then formulate a plan to implement the necessary recommendations.
To cater to different industries and multiple phases of development, PDPC created two checklists addressing various data breaches. With the aim of implementing best practices from the very beginning, the first checklist focuses on application security in the development and support phase and aims to tackle prevalent coding issues.
Meanwhile, the second checklist covers infrastructure and system security and offers recommendations to address the four other ICT gaps explained in the handbook. Combined, the two checklists were designed to help companies pre-empt and prepare solutions for a wide range of cyber security attacks or problems.
Because data protection issues vary from case to case, it is essential for your company to tailor the recommendations to your own ICT systems to ensure that they are effective. With the help of the available guides and checklists, PDPC makes setting up and maintaining robust data protection infrastructure a safe, secure, and simple task.
PDPC regularly publishes and updates resources that help organisations harness the power of data ethically while maintaining customer trust. With PDPC’s handbook and checklists, businesses can get informed about their cyber security, prevent online scams, and learn how to keep their data safe. Find out more about these resources here.


.webp)