In the electronic world, hand-written signatures can be replaced by digital signatures. Like written signatures, digital signatures may be used to establish the identity of a party or to make legal commitments. In addition, digital signatures can also be used to guarantee that the contents of a file or message have not been altered. The Electronic Transactions Act provides for the recognition of digital signatures under Singapore law.
For digital signatures to work, a trusted third party known as a Certification Authority (CA) is needed to issue digital certificates that certify the electronic identities of users and organisations. Before issuing a digital certificate, the CA performs an identity verification on the user or business entity. The CA acts like a trusted electronic notary, telling everyone who the valid users are and what their digital signatures should look like. With a certified electronic identity, an Internet user's digital signatures will then be recognised by parties involved in electronic transactions like Internet banking, online shopping and online information subscription services. The whole system of digital certificates, certificate servers and CAs is collectively known as a Public Key Infrastructure (PKI).
Digital signatures based on digital certificates issued by licensed CAs are automatically considered to be trustworthy and recognised by the law. Just like written signatures, they can be used to sign contracts or to purchase goods and services. To prevent forgery, digital signatures are created using a personal secret code, known as the signing key, which is usually stored in a secure device like a smart card. It is important that the signing key be kept private at all times so that no one else can forge your digital signatures. Loss of a signing key must be reported to the certification authority immediately.
Technical Inset
Digital signatures are created using a mathematical technique called cryptography. Cryptography is the science of disguising information by transforming a piece of data into something that seems totally random. The transformation process, known as encryption, usually involves an electronic key, which is just a string of digital bits functioning like a key to a lock in the physical world. Encrypting a piece of data is like putting the data into a safe and locking it with a key. By performing the reverse transformation (decryption), which may require the same key or a different key, the original data can be retrieved. Digital signature uses public key cryptography, a kind of cryptographic system involving two electronic keys. In public key cryptography, one key is kept private to the user while the other key is made known to the general public.
Suppose Alice wants to sign an electronic contract to be sent to Bob (please see Figure 1). She uses a signing system in conjunction with her signing key (private key) to create a digital signature based on the contract. On receiving the digital signature, Bob uses a verification system with Alice's verification key (public key) to verify that the contract was indeed signed by Alice. The system can determine that the signature has been created by Alice because only Alice's signing key could have generated the signature, and Alice is the only person who possesses the signing key. Hence, it is important that the signing key be kept private since anyone besides Alice who has a copy of her signing key will be able to forge her digital signatures. The signing key is usually stored in a smart card that is protected by a password. Loss of a private key must be reported to the certification authority immediately.

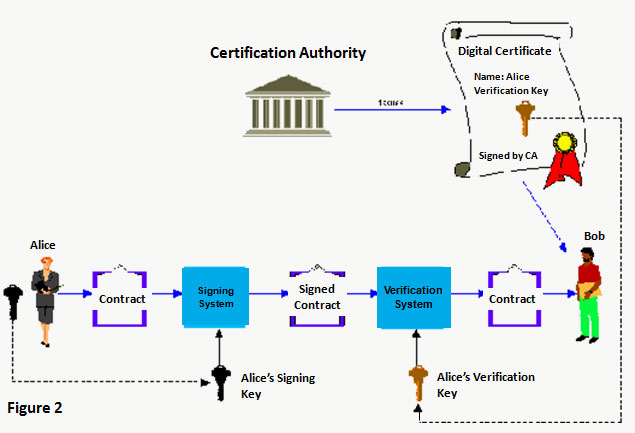
For the above scenario to work, Bob will need to have a trusted copy of Alice's verification key. This can be done by having a trusted third party known as a Certification Authority (CA). The CA issues digital certificates, which are electronic documents that tie each person's or organisation's identity to his/her public verification key. These digital certificates are signed by the CA, so that users can verify that the certificates are authentic. Figure 2 depicts a more complete picture of the digital signing and verification process. Bob checks that the digital certificate belongs to Alice and has been signed by a trusted CA. He then uses the enclosed verification key to verify Alice's digital signature. The digital certificate, used in conjunction with the private signing key, serves as a form of electronic identification, much like a digital passport.


.webp)