
By Izo Lopez
With online experiences full of ads and sponsored posts vying for our attention, businesses are turning to data analytics to gain an edge and win the attention of consumers. Spanning both physical and virtual business decisions, data has become the world’s most valuable resource—more so than oil. Each tap, swipe and purchase allows companies to collect data that can help improve business. But how can we be sure that our data is kept safe?
In 2012, Singapore put into place the Personal Data Protection Act (PDPA) to regulate the collection, use and disclosure of personal data. Earlier this year, the amended PDPA took effect, addressing the Republic’s evolving digital economy needs and providing guidelines for both consumers and businesses in better protecting personal data.
To help businesses stay accountable and updated with the changes, the Personal Data Protection Commission (PDPC) refreshed the content of two existing guides on data protection to align with the amendments to the PDPA and support businesses in implementing personal data protection policies and processes.
The first guide aims to help organisations develop or improve practices in accountability through the implementation of a Data Protection Management Programme (DPMP). In this article, learn about the various steps businesses can take to protect data through the DPMP, including: establishing governance and assessing risks, developing policy and practices, putting the processes into place and finally ensuring regular audits, reviews and revisions.
Meanwhile, the other guide provides an introductory outline on how to address specific personal data protection risks through conducting a Data Protection Impact Assessment (DPIA) for their systems and processes. Later on, read about the Data Life Cycle, which maps out the six phases involved in the DPIA.

Setting up a culture of accountability
Accountability is an overarching principle in the PDPA. To demonstrate accountability, organisations must develop policies, inform and communicate to staff about these policies and appoint a data protection officer (DPO) who ensures that the implemented policies are in compliance with the PDPA. The DPMP encompasses these strategies and guides organisations as they seek to effectively protect data through a four-step framework that they can tailor-fit to better suit their unique contexts.
The first of four steps, ‘Governance and Risk Assessment’, emphasises how management can champion personal data protection.
While personal data may be shared between departments and teams when required, the organisational policies will ensure that all customer data is used in compliance with the PDPA. Additionally, a culture of accountability can trickle down from leaders to staff through company-wide training or regular risk assessments to identify risks like new initiatives or policies that might not comply with PDPA.
In the ‘Policy and Practices’ step, businesses will be asked to consider some general questions to guide their policy implementation. By putting in place clear practices, organisations will also be able to clearly communicate these policies to internal stakeholders like staff and external parties like vendors and customers.
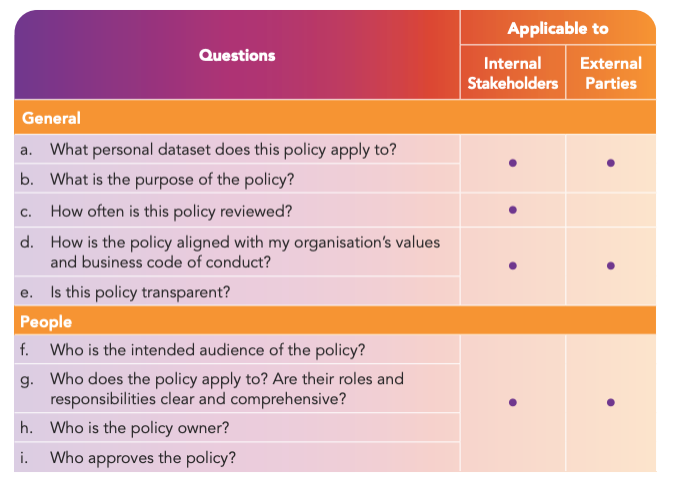
To help organisations design policies, the DPMP guides the organisation through questions such as the data types to be protected and the appropriate level of protection. This section also includes detailed examples, with a proposed situation and recommendations so that companies are aware of the different facets they might need to consider.
Continuous security improvement
The work of securing data does not, however, stop at the creation of new practices and policies. In the ‘Processes’ section, risks identified in the previous section form the basis of checklists and data inventories. It also suggests other mechanisms to safely collect and store data and make data breach reporting easier.
To help establish a clear process for handling data breaches, the guide conveniently provides a handy acronym: CARE, which represents Containing the breach, Assessing the risk, Reporting the incident and Evaluating the response and recovery to prevent future breaches.

The last step, ‘Maintenance’, encourages businesses to regularly review their data protection policies and processes. Instead of only reviewing policies when there is a breach, the PDPC recommends regular audits, reviews and revisions.
All in all, understanding how each step applies in the business context could go a long way towards actively helping organisations protect against data breaches and other risks. With the DPMP guide, organisations can establish robust personal data protection infrastructure with ease. For a more comprehensive guide on managing data breaches, the PDPC also has a Guide on Managing and Notifying Data Breaches Under the PDPA with more detailed information.
You can never be too secure
The PDPC’s DPIA guide goes hand in hand with the DPMP manual by providing businesses with a simple, six-step process for auditing data protection policies and determining risks.
Before beginning, businesses must assess the initial need for a DPIA. Next, the company should plan a DPIA by identifying parameters like scope, frameworks, parties involved and timeline. After developing a plan, map out the flow of relevant personal data involved in the project or policy to be audited. To fully illustrate the point, the guide offers an example of a website administrator who led a DPIA by consulting various departments about how they will access, use and store the collected data from a project.
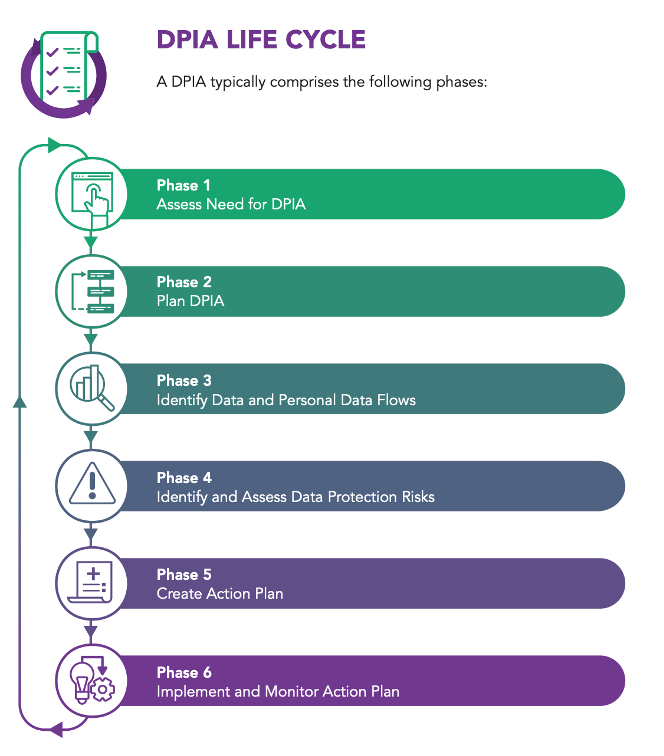
Data protection risks should then be identified by comparing the project against PDPA requirements, and other specific analyses of potential gaps, especially so if there are new changes, be it strategic, operational or relating to their business structure. Finally, businesses can use the insights gathered to develop and implement an action plan and later evaluate the outcome.
Ultimately, there is no one-size-fits-all solution for every company but if businesses follow both the DPMP and DPIA as well as tailor data protection plans to their unique needs, they can be assured of PDPA compliance—while consumers can be assured that their personal data is kept safe.
Find out more about the PDPC and personal data accountability. Meanwhile, view and download the two comprehensive guides through these links:
Data Protection Management Programme (DPMP) guide
Data Protection Impact Assessment (DPIA) guide


.webp)